Setup EAP-TLS, MSCHAPv2 authentication for Airtame devices within an enterprise environment (using Radius server, certificates).
This article serves to give an overview of how to set up authentication for Airtame devices within an enterprise environment. The article is divided into different sections that will detail how to set up Protected Extensible Authentication Protocol (PEAP) with MSCHAPv2 (EAP-MSCHAPv2) or EAP-TLS using Windows Certificate Authority servers and how to convert the certificates using OpenSSL.
Note this guide is written for an organization’s IT/Security department and gives specific details to create service accounts within Active Directory and to create client-side certificates for the Airtame. Please consult your IT department before making any changes to your network or security posture.
What is EAP-MSCHAPv2?
EAP-MSCHAPv2 is the most common form of PEAP used in enterprise networks today. Microsoft’s Challenge Handshake Authentication Protocol is used as the inner authentication method which means that through a TLS tunnel, the Airtame will authenticate with a service account that you will create in Active Directory against your RADIUS server. If you wish to use 802.1x, EAP-MSCHAPv2 is easy to implement and troubleshoot. For more information about EAP-MSCHAPv2, please reference RFC 2759 from the Internet Engineering Task Force (IETF).
What is EAP-TLS?
EAP Transport Layer Security (EAP-TLS), defined in RFC 5216, is an IETF open standard that uses the Transport Layer Security (TLS) protocol, and is well-supported among wireless vendors. EAP-TLS is the original, standard wireless LAN EAP authentication protocol.
EAP-TLS is still considered one of the most secure EAP standards available, although TLS provides strong security only so long as the user understands potential warnings about false credentials and is universally supported by all manufacturers of wireless LAN hardware and software.
Unlike most TLS implementations of HTTPS, such as on the World Wide Web, most implementations of EAP-TLS require client-side X.509 certificates without giving the option to disable the requirement, even though the standard does not mandate their use.
The requirement for a client-side certificate, however unpopular it may be, is what gives EAP-TLS its authentication strength and illustrates the classic convenience vs. security trade-off. With a client-side certificate, a compromised password is not enough to break into EAP-TLS enabled systems because the intruder still needs to have the client-side certificate; indeed, a password is not even needed, as it is only used to encrypt the client-side certificate for storage. The highest security available is when the "private keys" of client-side certificates are housed on smart cards or in certificate stores. This is because there is no way to steal a client-side certificate's corresponding private key from a smart card or certificate store without stealing the card or device itself. It is more likely that the physical theft of a smart card or device would be noticed (and the smart card immediately revoked) than a (typical) password theft would be noticed.
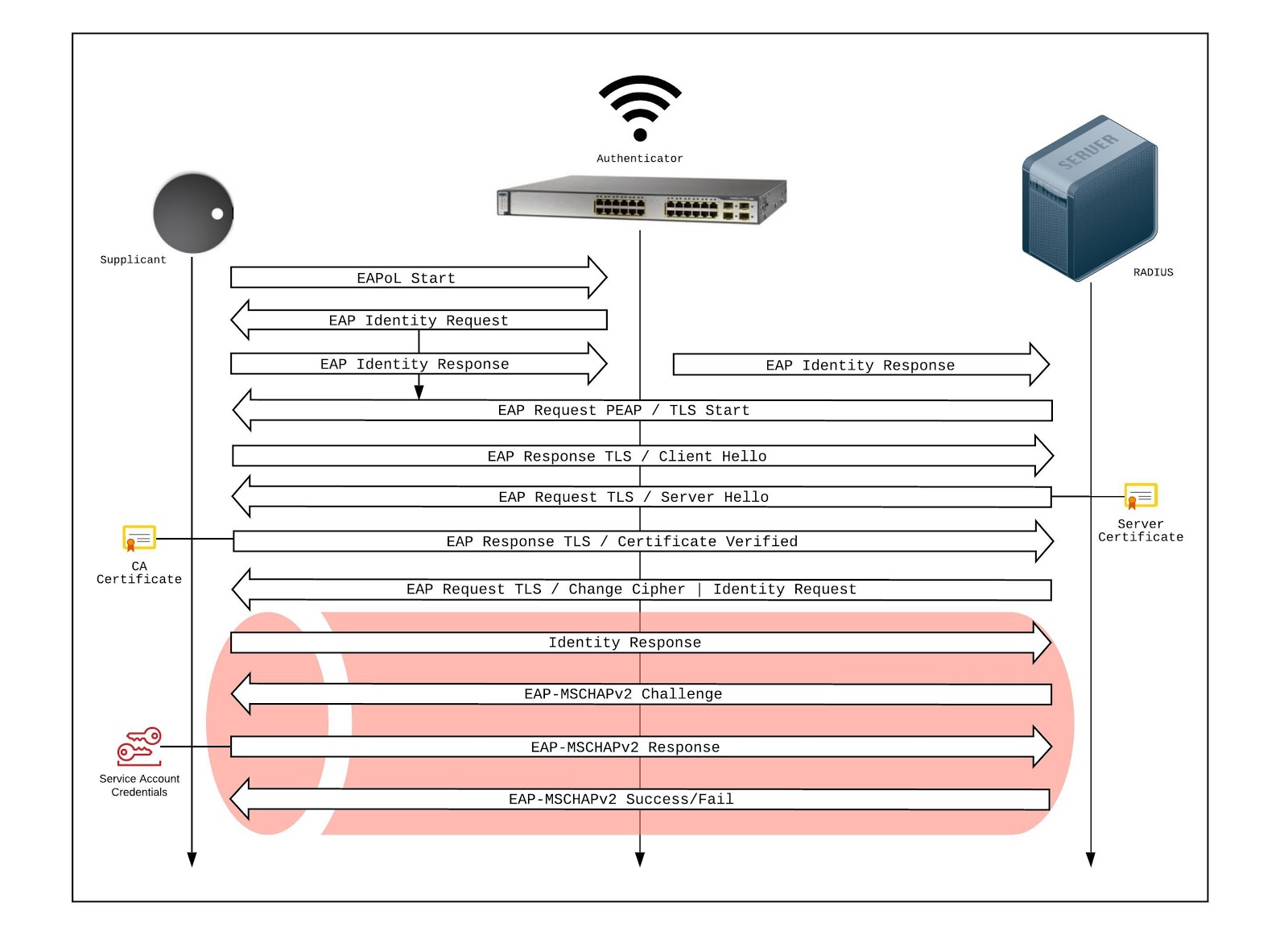
Below is the signal flow for EAP-TLS and the authentication procedure for EAP-TLS:
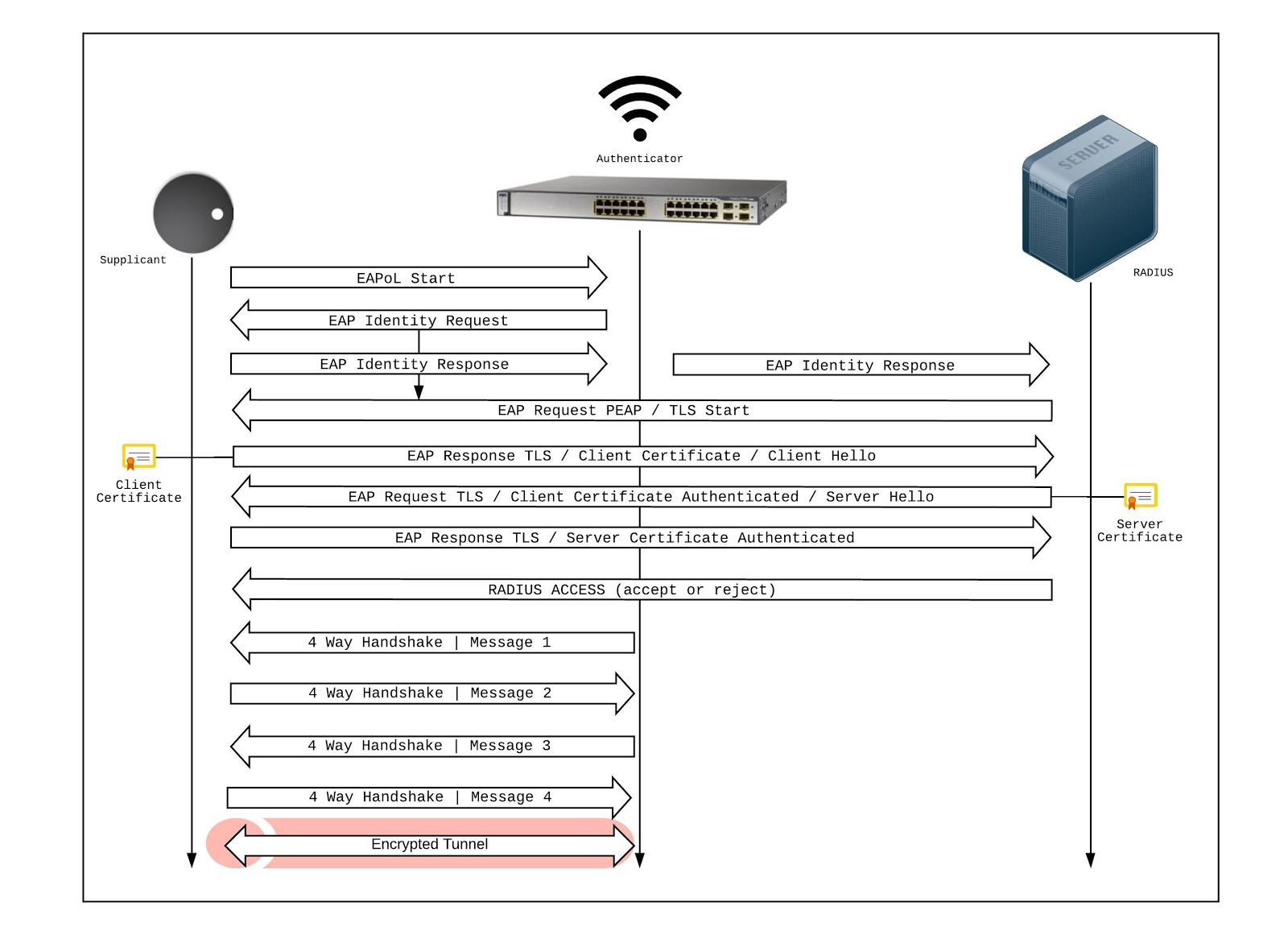
The following is the procedure for setting up EAP-TLS to work with Airtame. In this document, we will be using Windows Server 2016 with the Directory Services role installed, a Windows Server 2016 with the Certificate Authority role installed, and a Windows Server 2016 with the Network Protection and Access Services (NPAS) role installed to be the RADIUS server. OpenSSL will be used to extract the private key from the PKCS12 file and to change file formats.
Creating the Airtame service account in Active Directory
A successful EAP-TLS implementation will require the person setting this up to have “domain admin” access to Active Directory.
1. The first step will be to create a managed service account for the Airtame. It’s possible to either create a shared service account for all Airtame devices on your network or to create individual service accounts for each of the Airtames. This requirement will be applicable to the organization’s security policy.
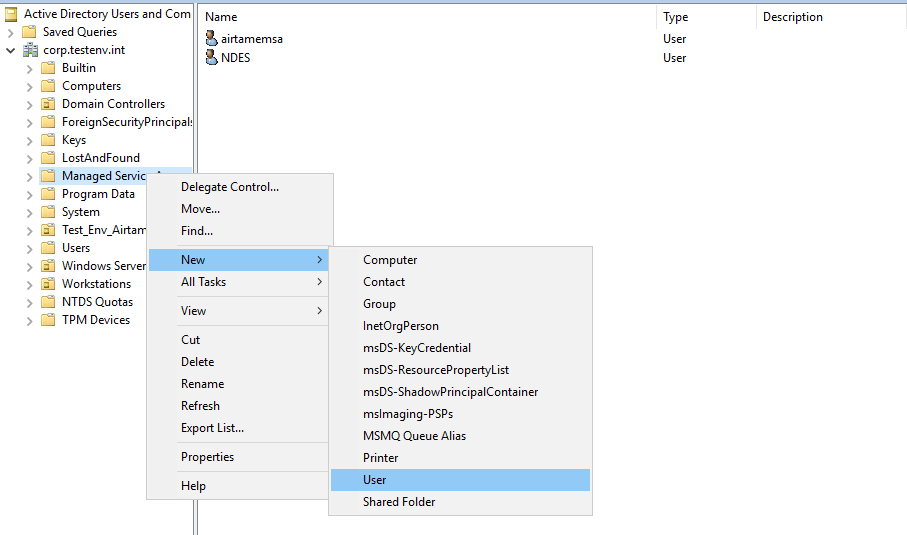
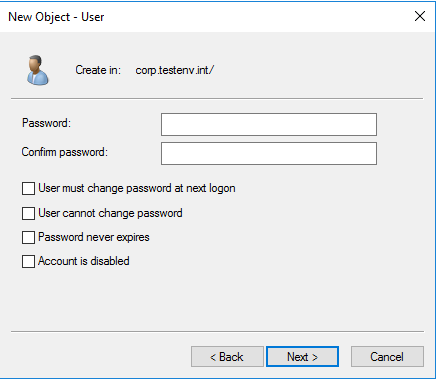
After the New User window opens, give the Airtame a unique name and populate the appropriate fields, and hit ‘next’.
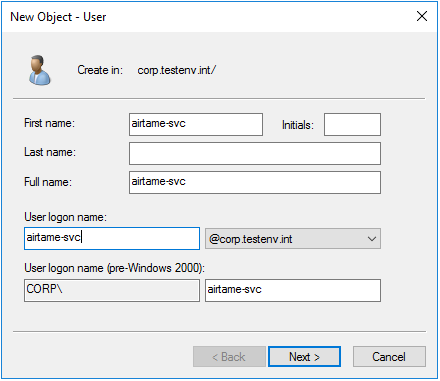
Enter a unique password and untick the box that says “User must change password at next logon”. Then click the "Next" button and click finish in the next window.
Setting up your RADIUS server to authenticate your Airtame
EAP-MSCHAPv2 or EAP-TLS can be used in WPA2-Enterprise networks using 802.1x to authenticate users. EAP-MSCHAPv2 authenticates the service account username/password to authenticate against your RADIUS server. EAP-TLS uses certificates to allow the Airtame and your RADIUS server to mutually authenticate and mutually verify the server (RADIUS) and the host (Airtame). I will be using a server running Windows Server 2016 with the Network Policy and Access Services role (NPAS) to function as the RADIUS server in our example. We will configure the Connection Request Policies and the Network Policies.
Creating the Connection Request Policy
-
Log into your NPAS server and open the Network Policy Server console.
-
Navigate to NPS(Local)>Policies>Connection Request Policies.
-
Right-click on Connection Request Policies and choose New.
-
On Specify Connection Policy Name and Connection Type enter a Policy name: and click Next.
-
On Specify Conditions click Add.
-
Select NAS Port Type as a condition.
-
For NAS Port Type check Wireless - IEEE 802.11 and Wireless - Other click on OK.
-
Click Next.
-
On Specify Connection Request Forwarding leave the defaults and click Next.
-
On Specify Authentication Methods leave the defaults and click Next.
-
On Configure Settings click Next.
-
Review the settings On Completing Connection Request Policy Wizard and click Finish.
-
Right-click the Connection Policy created and select Move up so its processing order is before any other policies.
Creating the Network Policy
-
Right-click Network Policies and select New.
-
On Specify Network Policy Name and Connection Type enter a Policy name: and click Next.
-
On Specify Conditions click Add.
-
Select NAS Port Type as a condition.
-
For NAS Port Type check Wireless - IEEE 802.11 and Wireless - Other, then click OK.
-
Click Next.
-
On Specify Access Permissions make sure Access granted is selected and click Next.
-
For EAP-TLS - On Configure Authentication Methods click Add and choose Microsoft: Smart Card or other certificates for Add EAP and click OK. For EAP-MSCHAPv2 - On Configure Authentication Methods click Add and choose Microsoft: Secured Password (EAP-MSCHAPv2).
-
Uncheck any boxes under Less secure authentication methods.
-
For EAP-TLS - Select Microsoft: Smart Card or other certificates for EAP types and click Edit.
-
For EAP-TLS - Verify the Certificate issued to drop down shows the correct certificate and issuer which is the Active Directory CA server. Then click OK.
-
Click Next.
-
On Configure Constraints click Next.
-
On Configure Settings, you will choose the RADIUS attributes. The RADIUS attributes vary from vendor to vendor, so please consult your wireless appliance administration guides.
-
Review the settings on Completing New Network Policy and click on Finish.
-
Right-click on the Network Policy created and select Move up so its processing order is before any other policies.
Please continue if you are using EAP-TLS. If you’re using EAP-MSCHAPv2, continue from the section “Obtaining your certificate authority (CA) certificate” below.
Creating your user certificate
1. After creating the Airtame service account, we will need to create the user certificate for the service account we just created. There are several different ways to do this. If your organization uses ‘Auto-Enrollment’ and allows private keys to be exportable, you can simply log into a domain joined computer with the service account we just created, and the certificate will automatically be created.
Note: However, if your organization doesn’t allow for private keys to be exportable, you will need to create a certificate template on the Certificate Authority server that will allow its private key to be exported. The link below will show you how to create a certificate template by duplicating a pre-configured template. While following the instructions in the link below, be sure to duplicate the ‘User’ certificate template rather than the ‘Web Server’ certificate template used in the example below. We want to duplicate the ‘User’ template as its intended purposes area for client authentication. Once you’ve created the template to allow the private key to be exported, repeat the instructions at the beginning of this step (step 2) and continue.
*Create and Manage Certificate Templates in Windows Server 2016
2. Once you’re logged into a domain computer with the service account you created, go to your Start Menu and type ‘mmc’ to open the console.
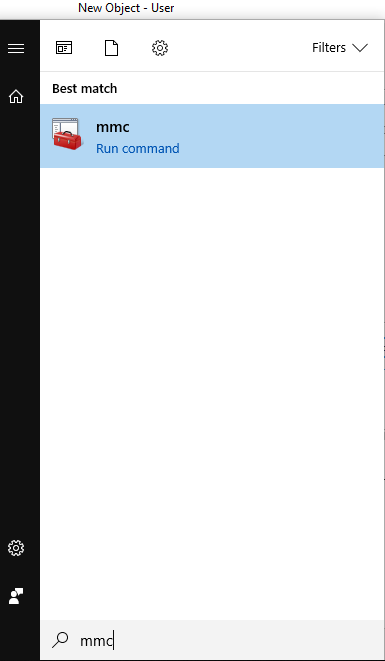
Next, click ‘File’ and click ‘Add/Remove Snap-in’. Select ‘Certificates’, click Add and click OK.
Open the "Personal" drop-down menu as detailed in the graphic below. Select "Certificates" and you will see the "airtame-svc" user account to the right. Right-click the certificate, choose "All Tasks" and click on "Export".
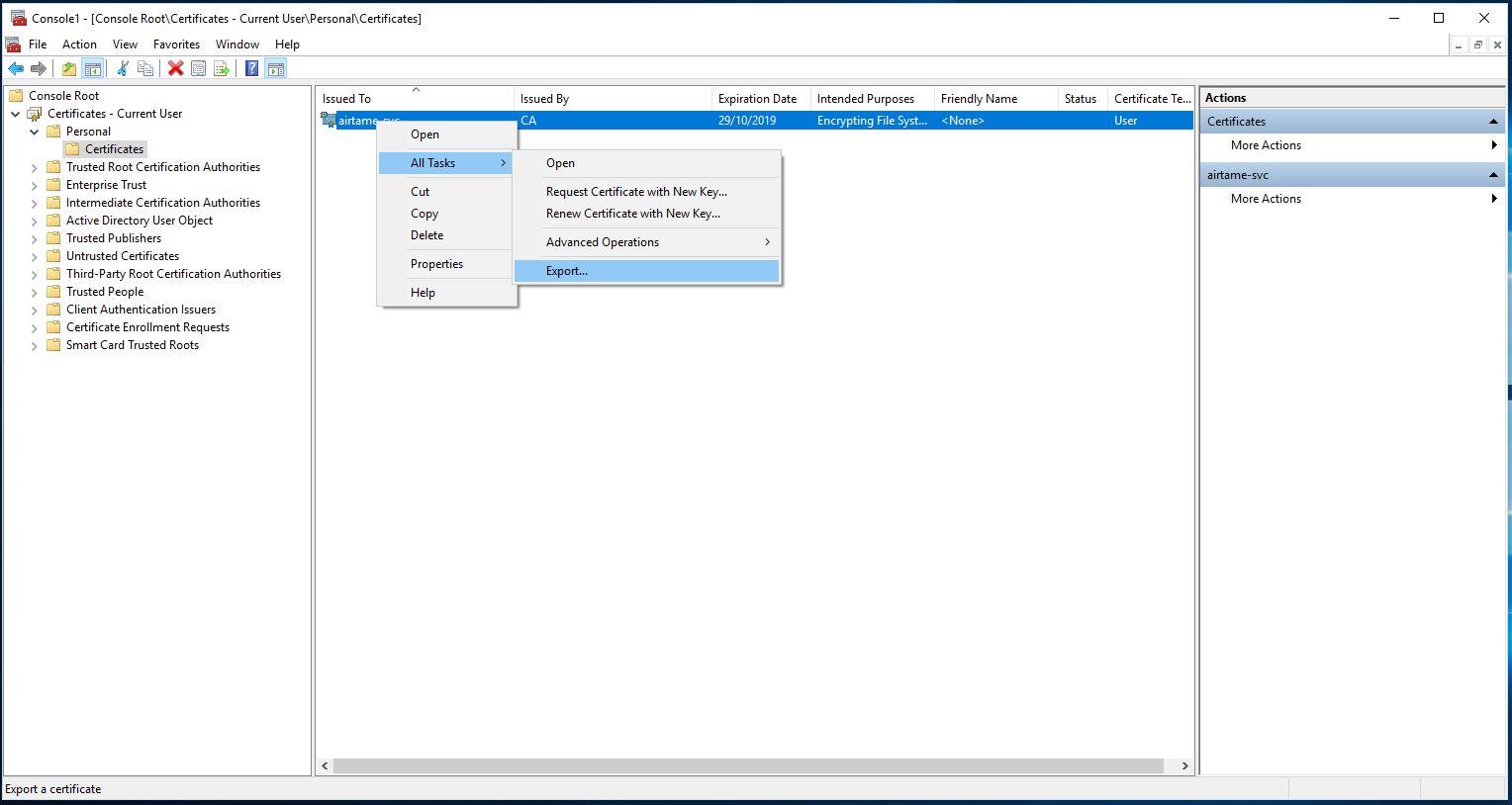
Once the Export window opens, click next and you will see the window below. Mark the tick boxes in the graphic and click "Next".
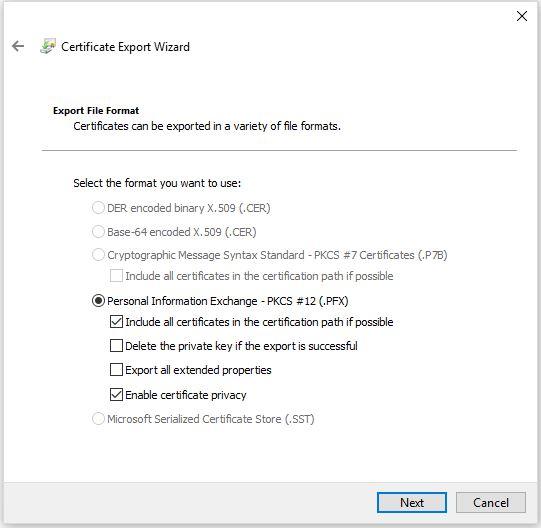
When you export the private key, you need to make some security considerations. You will need to restrict the certificate to specific users or users in an Active Directory group OR give the private key a password. In this example, I will give the private key a password. Once you complete this task, click "Next".
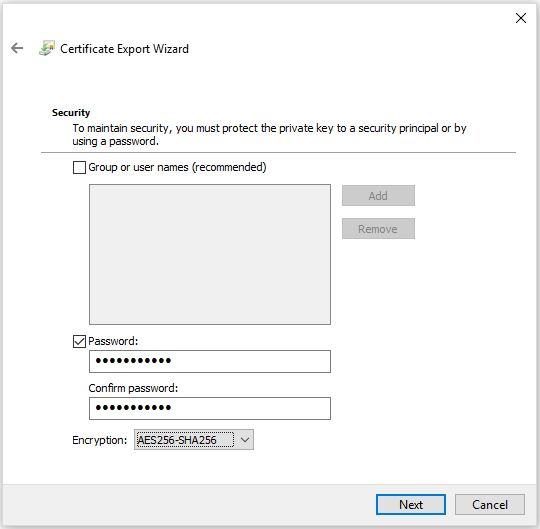
Now we will specify the name and path for our new PKCS12/.pfx file to be exported. Once finished, click "Next".
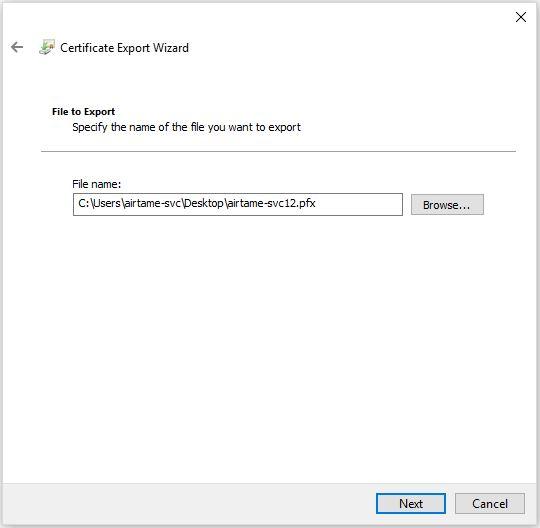
Now you are at the last page of the Certificate Export Wizard. Confirm the file is correct and that the line for "Export Keys" says "Yes". Then click "Finish".
3. At this time, we are going to extract the certificate and the private key from the .pfx (PKCS12) certificate in order to create two files. A file for the certificate and a file for the private key. In order to do this, we are going to use OpenSSL. Click on the start menu and type ‘CMD’. Once the application is visible, right-click the application and ‘Run as Administrator’.
From the Command Prompt, navigate to the directory where your OpenSSL installation is located and run the following commands. (Replace ‘filename’ with the path to your .pfx file and ‘key’ with the path where you want to place your key file). Note: be prepared to enter the private key password you created previously upon executing the following commands.
To export the private key from the .pfx file, enter the following OpenSSL command:openssl pkcs12 -in filename.pfx -nocerts -nodes -out key.pem
To export the certificate file from the .pfx file, enter the following OpenSSL command: openssl pkcs12 -in filename.pfx -clcerts -nokeys -out cert.pem
Obtaining your certificate authority (CA) certificate (required for both EAP-MSCHAPv2 and EAP-TLS)
Now that we have our certificate file and key file, we need to download the Certificate Authority certificate in Base64 format. The easiest way to retrieve the CA certificate is to access the "Web enrolment" page of your CA.
-
From the webpage, select "Download a CA certificate, certificate chain, or CRL".
-
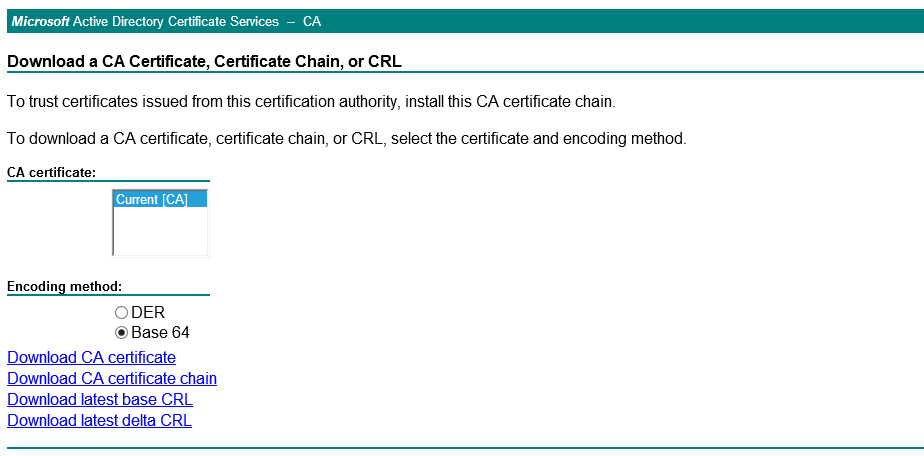
Choose Base64 and "Download CA certificate chain".
-
Once the CA certificate has been downloaded, we have to change the format of the CA certificate to become a PEM file. We will use OpenSSL to convert it:
Repeat the steps in step 3 to open OpenSSL. (Be sure to replace the word certificate with the full path to the CA certificate)Once you’re in the Command Prompt, enter the following command:
openssl pkcs7 -print_certs -in certificate.p7b -out certificate.pem
5. At this point we have all 3 certificates we need to set up EAP-TLS in the Airtame application.
Service account .pem file
Service account private key .pem file
CA certificate .pem file
If you’re using EAP-MSCHAPv2, enter the username, password and upload the CA certificate. As shown in the image below:
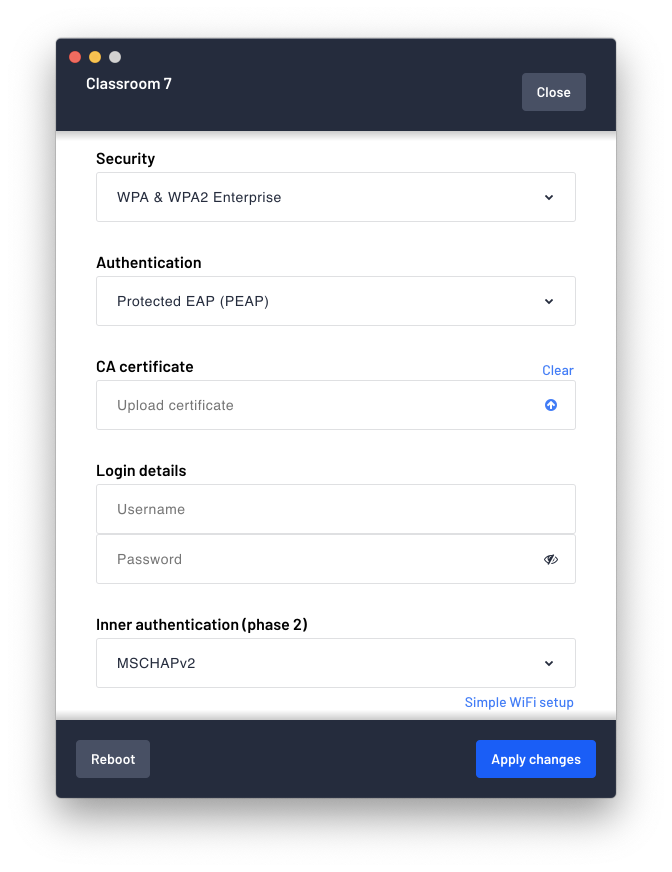
Open the Airtame application and begin the initial setup of the device
-
In the Airtame setup menu within the Airtame application, select the network type you wish to connect your Airtame device to (WiFi or ethernet) and fill out the fields below. The fields will appear automatically for WiFi networks, whereas you need to toggle them manually for an ethernet connection.

2. At this point, your Airtame device will get authenticated to your enterprise network. If you wish to configure more Airtames to connect to your enterprise network, simply reuse the CA certificate, host certificate, and key associated with the service account.